Note that airmon-ng has renamed your wlan0 adapter to mon0 (or wlan0mon if you are using a newer version of aircrack-ng). Step 2: Capture Traffic with airodump-Ng Now that our wireless adapter is in monitor mode, we have the capability to see all the wireless traffic that passes by in the air. Aircrack-ng Tutorial to Crack WPA/WPA2 Wifi networks. Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security like Monitoring, Attacking, Testing, and Cracking. All tools are command line which allows for heavy scripting. A lot of GUIs have taken advantage of this feature.
- Aircrack-ng Wpa2 Without Dictionary
- Wpa2 Psk Password Cracker
- Crack Wpa With Kali
- Metasploit
- Hack Wifi With Aircrack Ng
- Aircrack-ng Wpa2 Mac
Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat.
This is a brief walk-through tutorial that illustrates how to crack Wi-Fi networks that are secured using weak passwords. It is not exhaustive, but it should be enough information for you to test your own network's security or break into one nearby. The attack outlined below is entirely passive (listening only, nothing is broadcast from your computer) and it is impossible to detect provided that you don't actually use the password that you crack. An optional active deauthentication attack can be used to speed up the reconnaissance process and is described at the end of this document.
Aircrack-ng is a fork of the original Aircrack project. It can be found as a preinstalled tool in many Linux distributions such as Kali Linux or Parrot, which share common attributes as they are developed under the same project (Debian). Jun 01, 2018 wpa2-psk aircrack-ng windows aircrack-ng reaver windows aircrack-ng 1.2 rc4 (windows) aircrack-ng 1.2 rc1 (windows) running aircrack-ng on windows 10 aircrack-ng-1.2-rc4-win windows 7. Aircrack-ng is a complete suite of tools to assess WiFi network security.It focuses on different areas of WiFi security: Monitoring: Packet capture and export of data to text files for further processing by third party tools. Tutorial 7 - This exercise will demonstrate how to use a dictionary attack to crack WPA and WPA2 wireless security. It will show how to use airodump to capture traffic. Then how to use a.
If you are familiar with this process, you can skip the descriptions and jump to a list of the commands used at the bottom. For a variety of suggestions and alternative methods, see the appendix. neal1991 and tiiime have also graciously provided translations to this document and the appendix in Chinese if you prefer those versions.
DISCLAIMER: This software/tutorial is for educational purposes only. It should not be used for illegal activity. The author is not responsible for its use. Don't be a dick.
Getting Started
This tutorial assumes that you:
- Have a general comfortability using the command-line
- Are running a debian-based linux distro, preferably Kali linux (OSX users see the appendix)
- Have Aircrack-ng installed
sudo apt-get install aircrack-ng
- Have a wireless card that supports monitor mode (see here for a list of supported devices)
Cracking a Wi-Fi Network
Monitor Mode
Begin by listing wireless interfaces that support monitor mode with:
If you do not see an interface listed then your wireless card does not support monitor mode
We will assume your wireless interface name is wlan0 but be sure to use the correct name if it differs from this. Next, we will place the interface into monitor mode:
Run iwconfig. You should now see a new monitor mode interface listed (likely mon0 or wlan0mon).
Find Your Target
Start listening to 802.11 Beacon frames broadcast by nearby wireless routers using your monitor interface:
You should see output similar to what is below.
For the purposes of this demo, we will choose to crack the password of my network, 'hackme'. Remember the BSSID MAC address and channel (CH) number as displayed by airodump-ng, as we will need them both for the next step.
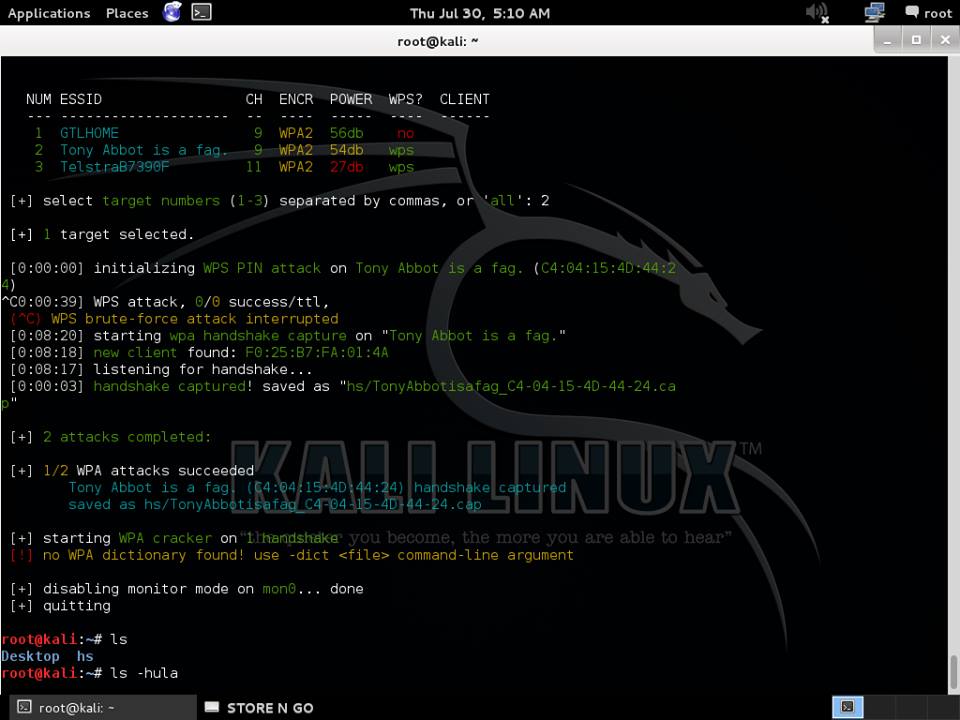
Capture a 4-way Handshake
WPA/WPA2 uses a 4-way handshake to authenticate devices to the network. You don't have to know anything about what that means, but you do have to capture one of these handshakes in order to crack the network password. These handshakes occur whenever a device connects to the network, for instance, when your neighbor returns home from work. We capture this handshake by directing airmon-ng to monitor traffic on the target network using the channel and bssid values discovered from the previous command.
Now we wait... Once you've captured a handshake, you should see something like [ WPA handshake: bc:d3:c9:ef:d2:67 at the top right of the screen, just right of the current time.
If you are feeling impatient, and are comfortable using an active attack, you can force devices connected to the target network to reconnect, be sending malicious deauthentication packets at them. This often results in the capture of a 4-way handshake. See the deauth attack section below for info on this.
Once you've captured a handshake, press ctrl-c to quit airodump-ng. You should see a .cap file wherever you told airodump-ng to save the capture (likely called -01.cap). We will use this capture file to crack the network password. I like to rename this file to reflect the network name we are trying to crack:
Crack the Network Password
The final step is to crack the password using the captured handshake. If you have access to a GPU, I highly recommend using hashcat for password cracking. I've created a simple tool that makes hashcat super easy to use called naive-hashcat. If you don't have access to a GPU, there are various online GPU cracking services that you can use, like GPUHASH.me or OnlineHashCrack. You can also try your hand at CPU cracking with Aircrack-ng.
Note that both attack methods below assume a relatively weak user generated password. Most WPA/WPA2 routers come with strong 12 character random passwords that many users (rightly) leave unchanged. If you are attempting to crack one of these passwords, I recommend using the Probable-Wordlists WPA-length dictionary files.
Cracking With naive-hashcat (recommended)
Before we can crack the password using naive-hashcat, we need to convert our .cap file to the equivalent hashcat file format .hccapx. You can do this easily by either uploading the .cap file to https://hashcat.net/cap2hccapx/ or using the cap2hccapx tool directly.
Next, download and run naive-hashcat:
Naive-hashcat uses various dictionary, rule, combination, and mask (smart brute-force) attacks and it can take days or even months to run against mid-strength passwords. The cracked password will be saved to hackme.pot, so check this file periodically. Once you've cracked the password, you should see something like this as the contents of your POT_FILE:
Where the last two fields separated by : are the network name and password respectively.
If you would like to use hashcat without naive-hashcat see this page for info.
Cracking With Aircrack-ng
Aircrack-ng can be used for very basic dictionary attacks running on your CPU. Before you run the attack you need a wordlist. I recommend using the infamous rockyou dictionary file:
Note, that if the network password is not in the wordfile you will not crack the password.
If the password is cracked you will see a KEY FOUND! message in the terminal followed by the plain text version of the network password.
Deauth Attack
A deauth attack sends forged deauthentication packets from your machine to a client connected to the network you are trying to crack. These packets include fake 'sender' addresses that make them appear to the client as if they were sent from the access point themselves. Upon receipt of such packets, most clients disconnect from the network and immediately reconnect, providing you with a 4-way handshake if you are listening with airodump-ng.
Use airodump-ng to monitor a specific access point (using -c channel --bssid MAC) until you see a client (STATION) connected. A connected client look something like this, where is 64:BC:0C:48:97:F7 the client MAC.
Now, leave airodump-ng running and open a new terminal. We will use the aireplay-ng command to send fake deauth packets to our victim client, forcing it to reconnect to the network and hopefully grabbing a handshake in the process.
You can optionally broadcast deauth packets to all connected clients with:
Once you've sent the deauth packets, head back over to your airodump-ng process, and with any luck you should now see something like this at the top right: [ WPA handshake: 9C:5C:8E:C9:AB:C0. Now that you've captured a handshake you should be ready to crack the network password.
List of Commands
Below is a list of all of the commands needed to crack a WPA/WPA2 network, in order, with minimal explanation.
Appendix
The response to this tutorial was so great that I've added suggestions and additional material from community members as an appendix. Check it out to learn how to:
- Capture handshakes and crack WPA passwords on MacOS/OSX
- Capture handshakes from every network around you with
wlandump-ng - Use
crunchto generate 100+GB wordlists on-the-fly - Spoof your MAC address with
macchanger
A Chinese version of the appendix is also available.
Attribution
Much of the information presented here was gleaned from Lewis Encarnacion's awesome tutorial. Thanks also to the awesome authors and maintainers who work on Aircrack-ng and Hashcat.
Overwhelming thanks to neal1991 and tiiime for translating this tutorial into Chinese. Further shout outs to yizhiheng, hiteshnayak305, enilfodne, DrinkMoreCodeMore, hivie7510, cprogrammer1994, 0XE4, hartzell, zeeshanu, flennic, bhusang, tversteeg, gpetrousov, crowchirp and Shark0der who also provided suggestions and typo fixes on Reddit and GitHub. If you are interested in hearing some proposed alternatives to WPA2, check out some of the great discussion on this Hacker News post.
Cracking WPA2wifi password is not really an easy thing to do,no you can't crack it with a click and there is no software that will give you the password without some hard work ...
don't run away still you can crack it with few steps here :) and we will do it using aircrack-ng

Requirements: To crack a wpa2-psk encrypted wifi password using aircrack-ng
1- Kali Linux or any Linux system with aircrack-ng installed
a- if you don't have aircrack-ng suite get it by this commend in terminal
2- a wireless network adapter that support monitor mode like
a- Alfa awus036ach
b- Alfa AWUS036H
c- wifiy-city 56G
d- and you can check this page here for usb wifi adapter with monitor mode
3- a word list comprising of all the possible different combination of pass-phrases
Now let's get to work
i will be using wifiy-city 56G card on Kali linux 2 sana
1) open up your terminal as root and type
this will show you all the networking interfaces connected to your device.
if your wireless network adapter is working fine you should see the ' wlan0 ' the name may change if you have more then one connected wireless adapter.
2) now to start monitor mode type
'airmon-ng' is a traffic monitoring tool
‘wlan0’ is your wireless interface
after this commend we started the monitor mode
as it's seen the monitor mode is working under wlan0mon , so this is your card name for now
in the red area a list of process id’s that cause trouble during the process so kill those processes by typing
in my case
now type ifconfig and this will show the newly set monitoring interface i.e, wlan0mon . in most case it will be mon0 .
3) to show list of available WiFi network type
Aircrack-ng Wpa2 Without Dictionary
airodump-ng is a wifi packets capturing toolWpa2 Psk Password Cracker
wlan0mon is my monitoring interface
airodump-ng will start capturing all packets and from the captured packets
select your target and note its ‘bssid’ (bssid = base service set identifier) and channel
then stop the capture using “cntrl+c“.
4) Start capturing the packets of your target network
type the following command
this will start the capturing of packets.
and if you get the handshake you wont need the aireplay command...
if you don't get the handshake yet
while the capturing of packets goes on, open a new terminal as root and type
aireplay-ng -0 0 -a <bssid> mon0
aireplay-ng = tool for deauthentication, fake authentication and other packet injections,
-0 = number associated for deauthentication,
0 = deauth count,
-a = bssid) here we are trying to send a deauthentication request.
In my case the command looks like
after few seconds stop it using cntrl+c.
now after we have successful captured the wpa handshake
5) Stop the capturing using cntrl+c and type “ls” that would bring up all the current directories and files.
Select the file with “.cap“extension and type the following command
aircrack-ng -w <full location of the word list> <name of the file>
aircrack-ng is a tool that helps in cracking the password
In my case the command looks like
For the Wordlist Check this Post Best Password dictionary
Now it starts finding suitable passphrase.
Crack Wpa With Kali
and now all you have to do is wait till you see the lovely news ( KEY Found ( your key is here ;) ).
Metasploit
all Step in few lines
have a great day :)